PrivacyNightmare
This page gathers articles, studies and reports on the risks and excesses caused by weak data protection.
Feel free to contribute by adding links to the "discussion" tab above or by directly editing this page. Articles in languages other than English and French go here also.
For documents in French click on "Français" above.
For current press and Quadrature press releases on the matter go to: https://www.laquadrature.net/en/Privacy
Contents
- 1 Studies on re-identification / de-anonymization
- 1.1 Mashable -Researchers can identify people behind 'anonymous' data 90% of the time (2 February 2015)
- 1.2 By Jonathan Mayer and Patrick Mutchler - MetaPhone: The Sensitivity of Telephone Metadata (12 March 2014)
- 1.3 EPIC Electronic Privacy Information Center Re-identification (continuously updated)
- 1.4 Wired - Security researcher de-anonymises users of French political forums (29 October 2013)
- 1.5 Nature - Unique in the Crowd: The privacy bounds of human mobility (25 March 2013)
- 1.6 University of Cambridge - Digital records could expose intimate details and personality traits of millions (11 March 2013)
- 1.7 Wired - Liking curly fries on Facebook reveals your high IQ (12 March 2013)
- 1.8 ArsTechnica - 'Anonymized' data really isn’t—and here’s why not (08 September 2009)
- 2 Public positions
- 2.1 The Guardian - Dear Google: open letter from 80 academics on 'right to be forgotten' (14 May 2015)
- 2.2 The New York Times - Letter to the Editor - Protecting our Privacy (4 November 2013)
- 2.3 WorldCrunch - European Academics Launch Petition To Protect Personal Data From "Huge Lobby" (13 March 2013)
- 2.4 More than 100 Leading European Academics are taking a position (February 2013)
- 3 The data industry
- 3.1 Big Brother Awards - The BigBrotherAward 2016 in the “Economy” category goes to the campaign platform change.org (2016)
- 3.2 The Washington Post - Google is tracking students as it sells more products to schools, privacy advocates warn (28 December 2015)
- 3.3 DW - Tagging along - is Adidas tracking soccer fans? (28 August 2014)
- 3.4 ZDNet - Apple steps up Health push as it begins talks with insurers (22 August 2014)
- 3.5 ArsTechnica - Why online tracking is getting creepier (12 June 2014)
- 3.6 The Telegraph - Drugs companies buy patient data register reveals (3 April 2014)
- 3.7 The Guardian - Yahoo, Google and Apple also claim right to read user emails (21 March 2014)
- 3.8 The New Scientist - Nest thermostat acquisition is Google's home invasion (15 January 2014)
- 3.9 Tech Crunch - Google’s Location History Browser Is A Minute-By-Minute Map Of Your Life (18 December 2013)
- 3.10 The Verge - LG admits its Smart TVs were ignoring privacy settings, promises firmware update to fix it (21 November 2013)
- 3.11 Wall Street Journal (blog) and Arstechnica - Facebook Tests Software to Track Your Cursor on Screen (30 October 2013)
- 3.12 The Verge - Judge dismisses suit against Google for bypassing Safari privacy settings (10 October 2013)
- 3.13 EU Observer - Hundreds of US companies make false data protection claims (8 October 2013)
- 3.14 Salon.com - Data hackers are watching you, Software inside your smartphone can follow you (8 October 2013)
- 3.15 Mother Jones - Here's How Twitter Can Track You on All of Your Devices (24 September 2013)
- 3.16 The Verge - City of London orders Renew to stop tracking citizens with its trash cans (12 August 2013)
- 3.17 The New York Times - Attention, Shoppers: Store Is Tracking Your Cell (14 July 2013)
- 3.18 Privatics - Paris Metro Tracks and Trackers: Why is the RATP App leaking my private data? (4 July 2013)
- 3.19 EU Observer - German data chief attacks credit-profile firms (25 April 2013)
- 3.20 CNN Money - What your zip code reveals about you (18 April 2013)
- 3.21 The American Prospect - Meet the Stalkers (15 April 2013)
- 3.22 RadioFreeEurope/RadioLiberty - Interview: 'It's Pretty Much Impossible' To Protect Online Privacy (8 April 2013)
- 3.23 SydneyMorningHerald - Facebook 'erodes any idea of privacy' (8 April 2013)
- 3.24 MemeBurn - How much are you worth to Facebook? (4 April 2013)
- 3.25 Computerworld - Judge awards class action status in privacy lawsuit vs. comScore (4 April 2013)
- 3.26 GigaOm - Why the collision of big data and privacy will require a new realpolitik (25 March 2013)
- 3.27 AdAge digital - Facebook to Partner With Acxiom, Epsilon to Match Store Purchases With User Profiles (22 February 2013)
- 3.28 The New York Times - Mapping, and Sharing, the Consumer Genome (Article on data broker Acxiom) (16 June 2012)
- 3.29 LA Times - Dad gets OfficeMax mail addressed 'Daughter Killed in Car Crash' (19 January 2014)
- 4 Data breach
- 4.1 EDRi - The biggest data breach in Turkish history (20 April 2016)
- 4.2 The Intercept - Massive Hack of 70 Million Prisoner Phone Calls Indicates Violations of Attorney-Client Privilege (11 November 2015)
- 4.3 Wired - OPM Now Admits 5.6m Feds’ Fingerprints Were Stolen By Hackers (23 September 2015)
- 4.4 France 24 - Japan's pension system hacked with 1.25 mn personal data leaks (01 June 2015)
- 4.5 Wired - Gmail Bug Could Have Exposed Every User’s Address (11 June 2014)
- 4.6 BBC - Hundreds of Met Police data protection breaches revealed (7 May 2014)
- 4.7 BBC - Abortion provider BPAS fined £200,000 for data breach (7 March 2014)
- 4.8 BBC - 'Treasure trove' of personal details found (26 February 2014)
- 4.9 The Guardian - Apple mobile devices at risk of hacking, firm says (22 February 2014)
- 4.10 The Australian - Immigration admits asylum-seeker privacy bungle, probes launched (19 February 2014)
- 4.11 BBC News - Kickstarter crowdfunding website hacked (16 February 2014)
- 4.12 ZD Net - Hackers access 800,000 Orange customers' data (3 February 2014)
- 4.13 WSJ - Coca-Cola: Stolen Laptops Had Personal Information of 74,000 (24 January 2014)
- 4.14 The Hacker News - Foursquare vulnerability that exposes 45 million users' email addresses (27 January 2014)
- 4.15 BBC News - Millions of passwords and email details stolen in Germany (21 January 2014)
- 4.16 Washington Post - Target says up to 70 million more customers were hit by December data breach (10 January 2014)
- 4.17 BBC News - Snapchat hack affects 4.6 million users (2 January 2014)
- 4.18 BBC News - Stolen Facebook and Yahoo passwords dumped online (4 December 2013)
- 4.19 Mediapart - «It was child's play»: how a hacker broke into MEPs' secret email accounts (21 November 2013)
- 4.20 Irish Times - Over 1.5 million affected by Ennis data breach (12 November 2013)
- 4.21 BBC news - 70,000 customers at risk from 'sophisticated criminal attack' (12 November 2013)
- 4.22 Ars Technica - Limo service hack spills compromising data about the rich and famous (4 November 2013)
- 4.23 Reuters - Adobe says source code, customer data stolen by hackers (3 October 2013)
- 4.24 Information is beautiful - World's Biggest Data Breaches (continually updated)
- 4.25 Infosecurity - Ubuntu Forum Hacked; 1.8 Million Accounts Compromised (22 July 2013)
- 4.26 Cambridge News - Massive personal data breach by police to G4S (23 April 2013)
- 4.27 Wired - Cloud Computing Snafu Shares Private Data Between Users (4 February 2013)
- 4.28 NURPA - SNCB Europe data leak involves more than one million customers (23 December 2012)
- 4.29 Bits - Yahoo Breach Extends Beyond Yahoo to Gmail, Hotmail, AOL Users (12 July 2012)
- 4.30 The Huffington Post - Yahoo Confirms 450,000 Accounts Breached, Experts Warn Of Collateral Damage (12 July 2012)
- 4.31 Network World - eHarmony data breach lessons: Cracking hashed passwords can be too easy (6 July 2012)
- 4.32 The New York Times - Lax Security at LinkedIn Is Laid Bare (10 June 2012)
- 4.33 The Register - 35m Google Profiles dumped into private database (25 May 2011)
- 4.34 The New York Times - After Breach, Companies Warn of E-Mail Fraud (Epsilon breach) (04 April 2013)
- 4.35 Wikipedia Article - Data breach: Major incidents
- 4.36 Wikipedia Fr - Piratage du PlayStation Network
- 5 Surveillance, the state and legislation addressing data collection
- 5.1 Big Brothrt Watch - Safe in Police Hands (July 2016)
- 5.2 The Globe and Mail - Spy agency accidentally shared Canadians’ data with allies for years (Jun. 01, 2016)
- 5.3 Just Security - EU-Funded Study: Electronic Mass Surveillance Fails – Drastically (14 October 2014)
- 5.4 BBC - Privacy fears over FBI facial recognition database (15 April 2014)
- 5.5 The New York Times - Data privacy: US revelations put heat on business (23 February 2014)
- 5.6 BBC News - Tesco petrol stations use face-scan tech to target ads (4 November 2013)
- 5.7 The New York Times - Europe Aims to Regulate the Cloud - (6 October 2013)
- 5.8 Bloomberg - U.K. Seeks to Block EU Data-Protection Plans That ‘Burden’ Firms (27 September 2013)
- 5.9 The Guardian Newspaper Britain accused of trying to impede EU data protection law (27 September 2013)
- 5.10 The Washington Post - NSA collects millions of e-mail address books globally (15 October 2013)
- 5.11 The Wall Street Journal - French Privacy Agency Moves to Sanction Google (27 September 2013)
- 5.12 Computer World - Google knows nearly every Wi-Fi password in the world (12 September 2013)
- 5.13 New York Times - Germany Fines Google Over Data Collection (22 April 2013)
- 5.14 Harvard Law Review: The Dangers of Surveillance (2012)
- 5.15 ZDNET : China's new data protection rules good step, but little bite (September 27, 2013)
- 6 Effects of loss of privacy on employment and credit worthiness
- 6.1 Ars Technica - Denied for that loan? Soon you may thank online data collection (11 October 2013)
- 6.2 On Device Research - Facebook costing 16-34s jobs in tough economic climate (29 May 2013)
- 6.3 CNN - Facebook friends could change your credit score (27 August 2013)
- 6.4 Spiegel Online - Puny Punishment for Goliath: Google Case Exposes Weak US Data Privacy Laws (10 August 2012)
- 7 General studies
- 7.1 The Guardian - Google can remotely bypass the passcode of at least 74% of Android devices if ordered (23 November 2015)
- 7.2 The Guardian - Obfuscation: how leaving a trail of confusion can beat online surveillance (24 October 2015)
- 7.3 International Journal of Communication - Exposing the Hidden Web: An Analysis of Third-Party HTTP Requests on One Million Websites(october 2015)
- 7.4 Ars Technica - Surveillance-based manipulation: How Facebook or Google could tilt elections (26 February 2015)
- 7.5 The Guardian - Facebook reveals news feed experiment to control emotions (30 June 2014)
- 7.6 Information.dk - For the NSA, espionage was a means to strengthen the US position in climate negotiations (30 January 2014)
- 7.7 George Washington University Law School - 'I've Got Nothing to Hide' and Other Misunderstandings of Privacy (2007)
- 7.8 Harvard Law Review - The Dangers of Surveillance (2012)
- 7.9 TED talks - The internet, the perfect tool for the surveillance state? Further reading (and watching) on the state of digital privacy (7 November 2013)
- 7.10 Electronic Frontier Foundation (EFF) - Who has your back? (continuously updated)
- 7.11 MIT Technological Review - The real privacy problem (22 October 2013)
- 7.12 Boston College Law Review - Big Data and Due Process: Toward a Framework to Redress Predictive Privacy Harms (13 September 2013)
- 7.13 The Boston Consulting Group - The Value of Our Digital Identity (20 November 2012)
- 7.14 The Cost of Reading Privacy Policies. I/S: A Journal of Law and Policy for the Information Society 2008 Privacy Year in Review issue. (with A. McDonald) http://lorrie.cranor.org/#publications Download: http://lorrie.cranor.org/pubs/readingPolicyCost-authorDraft.pdf
- 8 Other
- 8.1 EFF - Police Around the Country Regularly Abuse Law Enforcement Databases - 28 September 2016
- 8.2 Ars Technica - Major Qualcomm chip security flaws expose 900M Android users - 8 August 2016
- 8.3 The Guardian - Your battery status is being used to track you online - 2 August 2016
- 8.4 The Guardian - Chinese university puts CCTV in dormitories to encourage 'good study habits' (16 June 2016)
- 8.5 CBC - BlackBerry hands over user data to help police 'kick ass,' insider says (9 June 2016)
- 8.6 The Intercept_ - The Secret Surveillance Catalogue (17 December 2015)
- 8.7 WSJ - SocialRadar Balances Privacy With New Social Geolocation App (30 January 2014)
- 8.8 The New York Times - Letting Down Our Guard With Web Privacy (Psychology of divulging private information on the net) (30 March 2013)
- 8.9 The New Yorker - The Prism (24 June 2013)
Studies on re-identification / de-anonymization[edit]
Mashable -Researchers can identify people behind 'anonymous' data 90% of the time (2 February 2015)[edit]
All of the "sensitive information," such as name, credit card number and the time of the purchase were taken out of the equation — but the shoppers' activities had unique qualities nonetheless. The research team was able to accurately identify a shopper 90% of the time by using just four pieces of data on customer location, coupled with some other information about the shoppers.
By Jonathan Mayer and Patrick Mutchler - MetaPhone: The Sensitivity of Telephone Metadata (12 March 2014)[edit]
Is telephone metadata sensitive? The debate has taken on new urgency since last summer’s NSA revelations; all three branches of the federal government are now considering curbs on access. Consumer privacy concerns are also salient, as the FCC assesses telecom data sharing practices.
President Obama has emphasized that the NSA is “not looking at content.” “[T]his is just metadata,” Senator Feinstein told reporters. In dismissing the ACLU’s legal challenge, Judge Pauley shrugged off possible sensitive inferences as a “parade of horribles.”
On the other side, a number of computer scientists have expressed concern over the privacy risks posed by metadata. Ed Felten gave a particularly detailed explanation in a declaration for the ACLU: “Telephony metadata can be extremely revealing,” he wrote, “both at the level of individual calls and, especially, in the aggregate.” Holding the NSA’s program likely unconstitutional, Judge Leon credited this view and noted that “metadata from each person’s phone ‘reflects a wealth of detail about her familial, political, professional, religious, and sexual associations.’”
This is, at base, a factual dispute. Is it easy to draw sensitive inferences from phone metadata? How often do people conduct sensitive matters by phone, in a manner reflected by metadata?
EPIC Electronic Privacy Information Center Re-identification (continuously updated)[edit]
This website lists developments and reports on the question of re-identification.
Wired - Security researcher de-anonymises users of French political forums (29 October 2013)[edit]
A Swiss security researcher has managed to de-anonymise users of French political forums and blogs by exploiting a vulnerability in a service called Gravatar, which allows people to automatically use the same profile picture on all participating sites when posting anonymously.
Nature - Unique in the Crowd: The privacy bounds of human mobility (25 March 2013)[edit]
Apple recently updated its privacy policy to allow sharing the spatio-temporal location of their users with “partners and licensees” [('Apple and our partners and licensees may collect, use, and share precise location data, including the real-time geographic location of your Apple computer or device. This location data is collected anonymously in a form that does not personally identify you') ...] [I]t is estimated that a third of the 25B copies of applications available on Apple's App StoreSM access a user's geographic location and that the geo-location of ~50% of all iOS and Android traffic is available to ad networks. All these are fuelling the ubiquity of simply anonymized mobility datasets and are giving room to privacy concerns.
A simply anonymized dataset does not contain name, home address, phone number or other obvious identifier. Yet, if individual's patterns are unique enough, outside information can be used to link the data back to an individual. [...] We study fifteen months of human mobility data for one and a half million individuals and find that human mobility traces are highly unique. In fact, in a dataset where the location of an individual is specified hourly, and with a spatial resolution equal to that given by the carrier's antennas, four spatio-temporal points are enough to uniquely identify 95% of the individuals. [...]
University of Cambridge - Digital records could expose intimate details and personality traits of millions (11 March 2013)[edit]
Research shows that intimate personal attributes can be predicted with high levels of accuracy from ‘traces’ left by seemingly innocuous digital behaviour, in this case Facebook Likes. In the study, researchers describe Facebook Likes as a “generic class” of digital record - similar to web search queries and browsing histories - and suggest that such techniques could be used to extract sensitive information for almost anyone regularly online.
Researchers created statistical models able to predict personal details using Facebook Likes alone. Models proved 88% accurate for determining male sexuality, 95% accurate distinguishing African-American from Caucasian American and 85% accurate differentiating Republican from Democrat. Christians and Muslims were correctly classified in 82% of cases, and good prediction accuracy was achieved for relationship status and substance abuse – between 65 and 73%. [...]
The researchers also tested for personality traits including intelligence, emotional stability, openness and extraversion. While such latent traits are far more difficult to gauge, the accuracy of the analysis was striking. Study of the openness trait – the spectrum of those who dislike change to those who welcome it – revealed that observation of Likes alone is roughly as informative as using an individual’s actual personality test score.
Wired - Liking curly fries on Facebook reveals your high IQ (12 March 2013)[edit]
What you Like on Facebook could reveal your race, age, IQ, sexuality and other personal data, even if you've set that information to "private". [...] The research shows that although you might choose not to share particular information about yourself it could still be inferred from traces left on social media, such as the TV shows you watch or the music you listen to or the spiders that are afraid of you. [...]
ArsTechnica - 'Anonymized' data really isn’t—and here’s why not (08 September 2009)[edit]
This article makes the point that although information is "scrubbed" of all information that could personally identity an individual, this sounds better in theory than in practice. The article states that "87 percent of all Americans could be uniquely identified using only three bits of information: ZIP code, birthdate, and sex. [...]". The article referes to a paper by Ohm on "the surprising failure of anonymization."
"Such results are obviously problematic in a world where Google retains data for years, "anonymizing" it after a certain amount of time but showing reticence to fully delete it. "Reidentification science disrupts the privacy policy landscape by undermining the faith that we have placed in anonymization," Ohm writes. "This is no small faith, for technologists rely on it to justify sharing data indiscriminately and storing data perpetually, all while promising their users (and the world) that they are protecting privacy. Advances in reidentification expose these promises as too often illusory." [...]
Public positions[edit]
The Guardian - Dear Google: open letter from 80 academics on 'right to be forgotten' (14 May 2015)[edit]
It is one year since the European Court of Justice ruled that citizens have the right to request that Google remove links to information about them if these are out of date, misreprentative or irrelevant. But some of the world’s most expert academics claim that Google has not been transparent enough in how it is responding to requests for delisting, and 80 academics from around the world have written to the corporation demanding more transparency about its processes.
The New York Times - Letter to the Editor - Protecting our Privacy (4 November 2013)[edit]
Short letter to the editor from the president of the Electronic Privacy Information Center that sheds worry on the use of cloud computing given the recent revelations of access to data collected by private companies and accessed unlawfully by the NSA.
WorldCrunch - European Academics Launch Petition To Protect Personal Data From "Huge Lobby" (13 March 2013)[edit]
This week, more than 90 leading academics across Europe launched a petition to support the European Commission’s draft data protection regulation, reports the EU Observer. The online petition, entitled Data Protection in Europe, says “huge lobby groups are trying to massively influence the regulatory bodies.” The goal of the site is to make sure the European Commission’s law is in line with the latest technologies and that the protection of personal data is guaranteed. [...]
More than 100 Leading European Academics are taking a position (February 2013)[edit]
A position paper that puts forth a series of arguments that argue generally in favour of stronger protection for personal data. The document is available in several European languages. The arguments include perspectives on affects on innovation and competitiveness and raises the question of how to correct or best ways to legislate on this topic making reference to legislation currently in front of the European Institutions.
The data industry[edit]
Big Brother Awards - The BigBrotherAward 2016 in the “Economy” category goes to the campaign platform change.org (2016)[edit]
The BigBrotherAward 2016 in the “Economy” category goes to the campaign platform change.org represented by the Berlin branch of the US company of the same name because it uses personally identifiable information of people who signed petitions for the company’s own business purposes in varied and non-transparent ways. Based on information about the petitions somebody signed, this company creates profiles e.g. on political opinion, position in society, social situation – and it uses these for its own profit. As a matter of fact, change.org is not a non-profit social movement in digital form, it is a commercial enterprise whose business model focuses on the use and exploitation of sensitive personal information as well as on trading e-mail addresses.
The Washington Post - Google is tracking students as it sells more products to schools, privacy advocates warn (28 December 2015)[edit]
In public classrooms across the country, the corporate name that is fast becoming as common as pencils and erasers is Google. More than half of K-12 laptops or tablets purchased by U.S. schools in the third quarter were Chromebooks, cheap laptops that run Google software. Beyond its famed Web search, the company freely offers word processing and other software to schools. In total, Google programs are used by more than 50 million students and teachers around the world, the company says. But Google is also tracking what those students are doing on its services and using some of that information to sell targeted ads, according to a complaint filed with federal officials by a leading privacy advocacy group.
DW - Tagging along - is Adidas tracking soccer fans? (28 August 2014)[edit]
Sportswear maker Adidas has equipped its bestselling German national team soccer jersey with RFID tags. The company says it can't track customers via the tag, but potential privacy and transparency issues remain.
ZDNet - Apple steps up Health push as it begins talks with insurers (22 August 2014)[edit]
With Apple's new Health app set to launch this year, the company has been in discussions with insurance companies about where it could fit into their business.
ArsTechnica - Why online tracking is getting creepier (12 June 2014)[edit]
"online marketers are increasingly seeking to track users offline as well, by collecting data about people's offline habits—such as recent purchases, where you live, how many kids you have, and what kind of car you drive. [...]
Tracking people using their real names—often called "onboarding"—is a hot trend in Silicon Valley. In 2012, ProPublica documented how political campaigns used onboarding to bombard voters with ads based on their party affiliation and donor history. Since then, Twitter and Facebook have both started offering onboarding services allowing advertisers to find their customers online.
The Telegraph - Drugs companies buy patient data register reveals (3 April 2014)[edit]
Drugs corporations including Bayer, Baxter, AstraZeneca and Roche are among dozens of private firms sold NHS patient information, as well as Bupa, the healthcare provider.
The Guardian - Yahoo, Google and Apple also claim right to read user emails (21 March 2014)[edit]
The New Scientist - Nest thermostat acquisition is Google's home invasion (15 January 2014)[edit]
[Sara Watson at Harvard University's Berkman Center for Internet and Society] believes Google is now a company obsessed with viewing everyday activities as "information problems" to be solved by machine learning and algorithms. Google's fleet of self-driving vehicles is just one example. The home is no different, and a Google-enabled smart home of the future, using a platform such as the Google Now app – which already gathers data on users' travel habits – could adapt energy usage to your life in even more sophisticated ways.
"Imagine Google Now knows you're on your way home," suggests Watson. "The thermostat can predict that you're going to be home in 10 minutes and it can get the heat going."
Tech Crunch - Google’s Location History Browser Is A Minute-By-Minute Map Of Your Life (18 December 2013)[edit]
Quick! Where were you last Tuesday at 6:35 PM? If you’re anything like me, your answer is probably along the lines of “I… have absolutely no idea.” Most people’s brains just don’t work that way. But odds are, Google knows. They probably know where you’ve been most other days, too. And they’ll happily show you, letting you relive your life one step at a time. If you carry any Google-filled gear (like, say, an Android phone or tablet), there was a prompt during the initial setup that asked if Google could transmit your location data back to the mothership. This is that data. You know how Google Now can auto-magically figure out where you work and warn you about traffic? This is the data that makes that possible (or at least a good chunk of it.)
The Verge - LG admits its Smart TVs were ignoring privacy settings, promises firmware update to fix it (21 November 2013)[edit]
After an LG Smart TV owner discovered that his television was surreptitiously gathering information about him without his permission, the company has admitted that its opt-out system wasn't doing what it promised.
Wall Street Journal (blog) and Arstechnica - Facebook Tests Software to Track Your Cursor on Screen (30 October 2013)[edit]
The blog on the Wall Street Journal and an article on Arstechnica that links to it (http://arstechnica.com/business/2013/10/facebook-may-start-logging-your-cursor-movements/) report that Facebook is developing technology that would allow them to track the movement of your mouse.
The Verge - Judge dismisses suit against Google for bypassing Safari privacy settings (10 October 2013)[edit]
A Delaware judge has dismissed a class-action lawsuit against Google for secretly storing Safari cookies even when users had opted out. In a ruling from yesterday, Judge Sue Robinson wrote that the plaintiffs — who had filed suit under a variety of privacy and anti-hacking laws — hadn't proved real harm under any of them, nor had they convincingly argued that Google had violated their legal rights.
EU Observer - Hundreds of US companies make false data protection claims (8 October 2013)[edit]
Hundreds of US-based companies handling EU citizens' data have lied about belonging to a data protection arrangement known as the Safe Harbour Framework
Christopher Connolly, a director at Galexia, an Australian-based consulting company on internet law and privacy, told the European Parliament’s civil liberties committee on Monday (7 October) that “many claims of Safe Harbour membership are false.”. […]
The Safe Harbour agreement, hammered out in 2000 between the European Commission and the US Department of Commerce, is supposed to ensure that firms follow EU data protection laws when processing the personal data of EU citizens. […]
Salon.com - Data hackers are watching you, Software inside your smartphone can follow you (8 October 2013)[edit]
A long article giving a good overview of some of the products on the market that allow anyone who buys them to access your laptop, smart phone etc. The article lists the names of companies involved and the products available.
Mother Jones - Here's How Twitter Can Track You on All of Your Devices (24 September 2013)[edit]
This detailed article discusses twitter's recent purchase of MoPub, a company that places advertisements on mobile devices. Twitter, the author argues, would be uniquely placed to help data collectors match the various bits of data they collect about the same person. As twitter is used on many different platforms, they might be in a position to match "the person who just visited XYZ.com on their phone" and the person "who just logged into YZ.fr" on their laptop. Which would of course give much more information to advertisers. The author highlights that twitter has had a good history respecting privacy but that the economics might be too strong.
The Verge - City of London orders Renew to stop tracking citizens with its trash cans (12 August 2013)[edit]
Apparently Londoners aren't fond of being tracked by public trash cans. Less than a month after Renew began anonymously collecting information about people walking past their Wi-Fi-enabled trash bins, the City of London has put a stop to the practice. “We have already asked the firm concerned to stop this data collection immediately, and we have also taken the issue to the Information Commissioner’s Office,” the City of London said in a statement. ”Irrespective of what’s technically possible, anything that happens like this on the streets needs to be done carefully, with the backing of an informed public.”
The New York Times - Attention, Shoppers: Store Is Tracking Your Cell (14 July 2013)[edit]
Article on shops tracking customer's movement in the store via cellphones. Interestingly, the article notes, contrary to the willing suspencion of privacy concerns, enough customers, when alerted to this, complained.
Privatics - Paris Metro Tracks and Trackers: Why is the RATP App leaking my private data? (4 July 2013)[edit]
Informative and technical article about RATP (the Parisian metro system) app on cell phone sending data that could identify the apps that you run on your phone to third parties.
EU Observer - German data chief attacks credit-profile firms (25 April 2013)[edit]
This article, after a quick overview of Germany's legals procedures against Google and Facebook, focuses on data collecting and selling companies. Schufa, which "holds data on 65 million people in Germany", there are other smaller companies that offer services that estimate how likely a person is to default on their debt/pay on time by using their address (aka your neighbourhood) and age. Although there is already legislation limiting some use of data in such a way, there is a loop hole currently being exploited and legislation should be on its way to address it.
CNN Money - What your zip code reveals about you (18 April 2013)[edit]
This article echoes the points that are few other articles already made concerning the existence of data brokers (the article makes mention in particular to Acxiom) and how their industry works. The article raises the question of what is considered 'personal' information and mentions the decision in a Massachusets court that Zip codes (Postal code) can/should be considered as personal information. In this state and California retailers can no longer request your zip code for promotional purposes. As a whole the article makes a good overview of issues around personal data and uses simple language to get the ideas across.
The American Prospect - Meet the Stalkers (15 April 2013)[edit]
A long informative article that describes the data industry and it's effects on society. It considers the history of credit records and the effect that the ability to keep records indefinitely, even after the public institutions have expunged them, by private company can have on peoples' lives.
It states that the "law has failed to keep up with the rapid expansion of data harvesting in the same way it has stepped in to protect other sensitive information like credit reports [...] There was a time not long ago, [...] when consumer credit files were riddled with erroneous data and speculation—and when Americans had no legal recourse to correct these mistakes."
"The most worrisome outcome of the data revolution—and the hardest to quantify—is the discrimination that follows in this treasure trove of information’s wake. “What's at stake," wrote Singer, "is the risk that wholesale data collection creates an algorithmic system that assigns some people better offers like low interest rates while using an invisible scoring system to prevent others from getting loans, insurance or jobs. The risk is discrimination by statistical inference."
RadioFreeEurope/RadioLiberty - Interview: 'It's Pretty Much Impossible' To Protect Online Privacy (8 April 2013)[edit]
From online companies tracking users' digital footprints to the trend for more and more data to be stored on cloud servers, Internet privacy seems like a thing of the past -- if it ever existed at all. RFE/RL correspondent Deana Kjuka recently spoke about these issues with online security analyst Bruce Schneier, author of the book "Liars and Outliers: Enabling the Trust Society Needs to Survive." [...]
"If [you use] Gmail, [then] Google has all of your e-mail. If your files are in Dropbox, if you are using Google Docs, [or] if your calendar is iCal, then Apple has your calendar. So it just makes it harder for us to protect our privacy because our data isn't in our hands anymore." "I don't know about the future, but my guess is that, yes. The big risks are not going to be the illegal risks. They are going to be the legal risks. It's going to be governments. It's going to be corporations. It's going to be those in power using the Internet to stay in power."
SydneyMorningHerald - Facebook 'erodes any idea of privacy' (8 April 2013)[edit]
Facebook Home for Android phones has been dubbed by technologists as the death of privacy and the start of a new wave of invasive tracking and advertising. [...] Prominent tech blogger Om Malik wrote that Home “erodes any idea of privacy”. “If you install this, then it is very likely that Facebook is going to be able to track your every move, and every little action,” said Mailk. “This opens the possibility up for further gross erosions of privacy on unsuspecting users, all in the name of profits, under the guise of social connectivity,” he said. [...]
MemeBurn - How much are you worth to Facebook? (4 April 2013)[edit]
The argument that hundreds of millions of people give away their personal data on social networks with absolutely no interest in the commercial value of that information does not make sense. It is simply the case that they don’t have the slightest idea. [...] According to Spiekerman: “Even if privacy is an inalienable human right it would be good if people were enabled to manage their personal data as private property.” It’s not only about “monetizing”. The earth is, happily, not that flat. But materializing privacy might help us to overcome the huge issues we have when it comes to the privacy of internet users, and finally social networks and marketing will profit from more knowledge and more trust in the use of personal data.
Computerworld - Judge awards class action status in privacy lawsuit vs. comScore (4 April 2013)[edit]
A federal court in Chicago this week granted class action status to a lawsuit accusing comScore, one of the Internet's largest user tracking firms, of secretly collecting and selling Social Security numbers, credit card numbers, passwords and other personal data collected from consumer systems. [...] To collect data, comScore's software modifies computer firewall settings, redirects Internet traffic, and can be upgraded and controlled remotely, the complaint alleged. The suit challenged comScore's assertions that it filtered out personal information from data sold to third parties, and of intercepting data it had no business to access. [...]
GigaOm - Why the collision of big data and privacy will require a new realpolitik (25 March 2013)[edit]
People’s movements are highly predictable, researchers say, making it easy to identify most individuals from supposedly anonymized location datasets. As these datasets have valid uses, this is yet another reason why we need better regulation. [...] One of the explicit purposes of Unique in the Crowd was to raise awareness. As the authors put it: “these findings represent fundamental constraints to an individual’s privacy and have important implications for the design of frameworks and institutions dedicated to protect the privacy of individuals.” [...]
AdAge digital - Facebook to Partner With Acxiom, Epsilon to Match Store Purchases With User Profiles (22 February 2013)[edit]
"Facebook is partnering with data giants including Epsilon, Acxiom and Datalogix to allow brands to match data gathered through shopper loyalty program to individual Facebook profiles, much like it's done previously with marketers' customer data from their CRM databases."
The New York Times - Mapping, and Sharing, the Consumer Genome (Article on data broker Acxiom) (16 June 2012)[edit]
Long article on the data broker Acxiom, second largest (in size?) after Epsilon. The article describes the history of the company, how it works, what type of data it holds, it's annual profits and how it has dealt with privacy concerns. On the other hand the article also explores privacy concerns of citizens, questions of how well the information is protected, data breaches (not much information on this), encryption of the website, racial and stereotyping of other kinds and that these businesses have little oversight nor regulation.
LA Times - Dad gets OfficeMax mail addressed 'Daughter Killed in Car Crash' (19 January 2014)[edit]
A dad who have lost his daughter in a car crash targeted by spam emails with subject "Daughter killed in a car crash"
Data breach[edit]
EDRi - The biggest data breach in Turkish history (20 April 2016)[edit]
About 50 million personal records of Turkish citizens have been made publicly available in a searchable database on the internet. Ironically, although the site that holds the database is open to the entire world, it is one of the 110,000 sites blocked by Turkish government and can only be accessed from Turkey via a virtual private network (VPN). The database contains personal information such as names, citizenship numbers, parent names and addresses of 49,611,709 citizens. This huge number involved makes the breach the most serious in Turkish history. By comparison: the Office of Personnel Management leak in April 2015 involved the personal records of 22 million public servants in the US.
The Intercept - Massive Hack of 70 Million Prisoner Phone Calls Indicates Violations of Attorney-Client Privilege (11 November 2015)[edit]
AN ENORMOUS CACHE of phone records obtained by The Intercept reveals a major breach of security at Securus Technologies, a leading provider of phone services inside the nation’s prisons and jails. The materials — leaked via SecureDrop by an anonymous hacker who believes that Securus is violating the constitutional rights of inmates — comprise over 70 million records of phone calls, placed by prisoners to at least 37 states, in addition to links to downloadable recordings of the calls. The calls span a nearly two-and-a-half year period, beginning in December 2011 and ending in the spring of 2014.
Wired - OPM Now Admits 5.6m Feds’ Fingerprints Were Stolen By Hackers (23 September 2015)[edit]
When hackers steal your password, you change it. When hackers steal your fingerprints, they’ve got an unchangeable credential that lets them spoof your identity for life. When they steal 5.6 million of those irrevocable biometric identifiers from U.S. federal employees—many with secret clearances—well, that’s very bad.
On Wednesday, the Office of Personnel Management admitted that the number of federal employees’ fingerprints compromised in the massive breach of its servers revealed over the summer has grown from 1.1 million to 5.6 million. OPM, which serves as a sort of human resources department for the federal government, didn’t respond to WIRED’s request for comment on who exactly those fingerprints belong to within the federal government. But OPM had previously confirmed that the data of 21.5 million federal employees was potentially compromised by the hack—which likely originated in China—and that those victims included intelligence and military employees with security clearances.
France 24 - Japan's pension system hacked with 1.25 mn personal data leaks (01 June 2015)[edit]
Japan's pension service said Monday it suffered a hack attack that led to 1.25 million cases of personal data being leaked. An employee opened an e-mail with a virus, triggering the release of client names, pension account numbers, birth dates and addresses, it said, adding that the breach was discovered last week.
Wired - Gmail Bug Could Have Exposed Every User’s Address (11 June 2014)[edit]
Until recently, anyone may have been able to assemble a list of every Gmail account in the world. All it would have taken, according to one security researcher’s analysis, was some clever tweaking of a web page’s characters and a lot of patience.
BBC - Hundreds of Met Police data protection breaches revealed (7 May 2014)[edit]
Data protection breaches at the Met Police including instances of officers assisting criminals and selling personal details have been revealed.
Results of a Freedom of Information request shows 300 police breaches between January 2009 and October 2013.
BBC - Abortion provider BPAS fined £200,000 for data breach (7 March 2014)[edit]
An abortion provider has been fined £200,000 for a data breach that revealed almost 10,000 people's details to a hacker.
BBC - 'Treasure trove' of personal details found (26 February 2014)[edit]
About 360 million account credentials including email addresses and passwords were reportedly uncovered [and] 1.25 billion email addresses without passwords. [...]
He said the credentials had been stolen in breaches yet to be publicly reported. The companies attacked could remain unaware until they were notified by third parties who found evidence of the hacking, he said.
The Guardian - Apple mobile devices at risk of hacking, firm says (22 February 2014)[edit]
A major flaw in Apple software for mobile devices could allow hackers to intercept email and other communications that are meant to be encrypted, the company has said, and experts say Mac computers are even more exposed.
The Australian - Immigration admits asylum-seeker privacy bungle, probes launched (19 February 2014)[edit]
Investigations have been launched into an immigration lapse which allowed access to the personal details of 10,000 asylum-seekers in Australia. [...]
The database, which was accessible through the department’s website, reportedly disclosed the full names, nationalities, locations and arrival information of every immigration detainee held on the mainland and on Christmas Island, as well as several thousand on community detention. It included a large cohort of children.
BBC News - Kickstarter crowdfunding website hacked (16 February 2014)[edit]
Online crowdfunding website Kickstarter has said that hackers obtained some of its customers' data. [...]
The hackers got some passwords, phone numbers and email addresses, but "no credit card data of any kind was accessed," he said.
ZD Net - Hackers access 800,000 Orange customers' data (3 February 2014)[edit]
Orange customers in France could see a spike in phishing attempts after hackers nabbed hundreds of thousands of customers' unencrypted personal data in an attack on the operator's website.
Hackers accessed the personal data of three percent of Orange's customers in France, the company confirmed, using the 'My Account' section of orange.fr.
According to local reports, the attack took place on 16 January, and affected nearly 800,000 individuals.
WSJ - Coca-Cola: Stolen Laptops Had Personal Information of 74,000 (24 January 2014)[edit]
Coca-Cola Co. said on Friday that personal information on as many as 74,000 employees, contractors and suppliers were on laptops that it said were temporarily stolen from its Atlanta headquarters.
The Hacker News - Foursquare vulnerability that exposes 45 million users' email addresses (27 January 2014)[edit]
A location based Social Networking platform with 45 million users,'Foursquare' was vulnerable to the primary email address disclosed. Foursquare is a Smartphone application that gives you details of nearby cafes, bars, shops, parks using GPS location and also tells about your friends nearby. According to a Penetration tester and hacker 'Jamal Eddine', an attacker can extract email addresses of all 45 million users just by using a few lines of scripting tool.
BBC News - Millions of passwords and email details stolen in Germany (21 January 2014)[edit]
The passwords and other details of 16 million email users in Germany have been stolen, the country's security agency has revealed. The Federal Office for Security said criminals had infected computers with software which allowed them to gather email addresses and account passwords.
Washington Post - Target says up to 70 million more customers were hit by December data breach (10 January 2014)[edit]
Target said Friday that the thieves who stole massive amounts of credit and debit card information during the holiday season also swept up names, addresses and phone numbers of 70 million customers, information that could put victims at greater risk for identity theft.
BBC News - Snapchat hack affects 4.6 million users (2 January 2014)[edit]
The usernames and phone numbers for 4.6 million Snapchat accounts have been downloaded by hackers, who temporarily posted the data online.
BBC News - Stolen Facebook and Yahoo passwords dumped online (4 December 2013)[edit]
More than two million stolen passwords used for sites such as Facebook, Google and Yahoo and other web services have been posted online.
Mediapart - «It was child's play»: how a hacker broke into MEPs' secret email accounts (21 November 2013)[edit]
A hacker using elementary computer equipment and what he described as “a few bits of knowledge that everyone is capable of finding on the internet” has succeeded in accessing confidential emails and personal files of Members of the European Parliament, their assistants and even the institution’s IT experts, Mediapart can reveal. The operation was, he said, mounted as a demonstration of the vulnerability of security at both the parliament in Strasbourg and also among many national administrations which use software, notably that of Microsoft, that experts have for years warned is exposed to espionage manipulations through fundamental - and what some suggest are possibly deliberate - flaws. While the scandal of mass surveillance employed by the US National Security Agency continues to unfold, Jérôme Hourdeaux reports on how major public institutions like the European Parliament continue to expose themselves to almost mundane intrusion of confidential data.
Irish Times - Over 1.5 million affected by Ennis data breach (12 November 2013)[edit]
More than 1.5 million people are now known to have had personal information compromised by a major security breach at a Co Clare-based company which manages customer loyalty schemes across Europe.
BBC news - 70,000 customers at risk from 'sophisticated criminal attack' (12 November 2013)[edit]
"Up to 70,000 people in Ireland who took advantage of a customer loyalty offer could have been victims of a "sophisticated criminal attack"."
Another case where data on customers of one company (in this case a holiday booking company) was stolen but in which the information obtained could jeopardize the security of their bank accounts.
Ars Technica - Limo service hack spills compromising data about the rich and famous (4 November 2013)[edit]
Information about famous and rich people has been posted online. Motivations are unclear but as Krebs reports, this breach and the publication of the data, exposes famous peoples' data and some of their potentially insalubrious behaviour. Refers to Krebs on security post: http://krebsonsecurity.com/2013/11/hackers-take-limo-service-firm-for-a-ride/.
Reuters - Adobe says source code, customer data stolen by hackers (3 October 2013)[edit]
Adobe Systems Inc said on Thursday that hackers had stolen source code to some of its most popular software and data about millions of its customers.
Adobe Chief Security Officer Brad Arkin said hackers also took information on 2.9 million Adobe customers, including their names, user identification numbers and encrypted passwords and payment card numbers.
UPDATE: Adobe Breach Impacted At Least 38 Million Users (29 October 2013)
But just this past weekend, AnonNews.org posted a huge file called “users.tar.gz” that appears to include more than 150 million username and hashed password pairs taken from Adobe. The 3.8 GB file looks to be the same one Hold Security CTO Alex Holden and I found on the server with the other data stolen from Adobe.
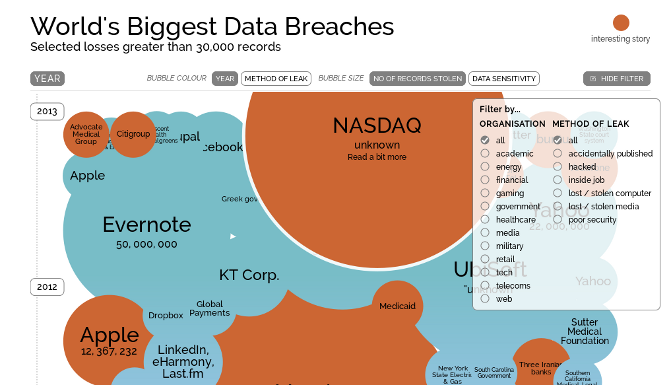
Information is beautiful - World's Biggest Data Breaches (continually updated)[edit]
Go to the website for an updated version of this image.
Infosecurity - Ubuntu Forum Hacked; 1.8 Million Accounts Compromised (22 July 2013)[edit]
The article gives details of the July 2013 hack of the Ubuntu Linux forum that defaced the forum's website and stole users' account information.
Cambridge News - Massive personal data breach by police to G4S (23 April 2013)[edit]
Small town version of the data breach kind. Good example of how insecure the whole system of data is. The Cambridgeshire police released information about their staff to another company that it was in contact with.
[edit]
A low-cost competitor to giants such as RackSpace and Amazon, DigitalOcean sells cheap computing power to web developers who want to get their sites up and running for as little as $5 per month. But it turns out that some of those customers — those who were buying the $40 per month or $80 per month plans, for example — aren’t necessarily getting their data wiped when they cancel their service. And some of that data is viewable to other customers. Kenneth White stumbled across several gigabytes of someone else’s data when he was noodling around on DigitalOcean’s service last week. White, who is chief of biomedical informatics with Social and Scientific Systems, found e-mail addresses, web links, website code and even strings that look like usernames and passwords — things like 1234qwe and 1234567passwd. [...]
NURPA - SNCB Europe data leak involves more than one million customers (23 December 2012)[edit]
For several weeks, personal details of more than one million customers of the train company SNCB Europe were available on-line. Although the exact search terms that lead to the original disclosure are unknown, these data were indeed accessible via a simple query in a search engine.
Bits - Yahoo Breach Extends Beyond Yahoo to Gmail, Hotmail, AOL Users (12 July 2012)[edit]
Yahoo confirmed Thursday that about 400,000 user names and passwords to Yahoo and other companies were stolen on Wednesday. A group of hackers, known as the D33D Company, posted online the user names and passwords for what appeared to be 453,492 accounts belonging to Yahoo, and also Gmail, AOL, Hotmail, Comcast, MSN, SBC Global, Verizon, BellSouth and Live.com users. [...] The hackers wrote a brief footnote to the data dump, which has since been taken offline: “We hope that the parties responsible for managing the security of this subdomain will take this as a wake-up call, and not as a threat.”
The Huffington Post - Yahoo Confirms 450,000 Accounts Breached, Experts Warn Of Collateral Damage (12 July 2012)[edit]
Security researchers warned Thursday that thousands of people could be vulnerable to hackers after Yahoo confirmed that about 450,000 usernames and passwords were stolen from one of the company's databases [...] Yahoo Voices contributors signed up using a variety of accounts: about 140,000 Yahoo addresses, more than 100,000 Gmail addresses, more than 55,000 Hotmail addresses and more than 25,000 AOL addresses. [...] A hacker group called D33D claimed responsibility for the disclosure of usernames and passwords belonging to Yahoo Voices' users. "We hope that the parties responsible for managing the security of this subdomain will take this as a wake-up call, and not as a threat," the group said in a statement. [...] Alex Horan, a senior product manager at CORE Security, criticized Yahoo for apparently storing usernames and passwords without encrypting them. "The bigger problem is these passwords were sitting there in the clear," Horan said. He added that encrypting passwords was "Security 101." "That’s mind-blowing that a company wouldn't do that," he said. [...]
Network World - eHarmony data breach lessons: Cracking hashed passwords can be too easy (6 July 2012)[edit]
Last month the dating site eHarmony suffered a data breach in which more than 1.5 million eHarmony password hashes were stolen and later dumped online by the hacker gang called Doomsday Preppers. The crypto-based "hashing" process is supposed to conceal stored passwords, but Trustwave's SpiderLabs division says eHarmony could have done this process a lot better because it only took 72 hours to crack about 80% of 1.5 million eHarmony hashed passwords that were dumped.
Cracking the dumped eHarmony passwords wasn't too hard, says Mike Kelly, security analyst at SpiderLabs, which used tools such as oclHashcat and John the Ripper. In fact, he says it was one of the "easiest" challenges he ever faced. There are many reasons why this is so, starting with the fact the cracked passwords may have been "hashed," but they weren't "salted," which he says "would drastically increase the time it would take to crack them." [...]
The New York Times - Lax Security at LinkedIn Is Laid Bare (10 June 2012)[edit]
Last week, hackers breached the site and stole more than six million of its customers’ passwords, which had been only lightly encrypted. [...]
What has surprised customers and security experts alike is that a company that collects and profits from vast amounts of data had taken a bare-bones approach to protecting it. The breach highlights a disturbing truth about LinkedIn’s computer security: there isn’t much. Companies with customer data continue to gamble on their own computer security, even as the break-ins increase.
“If they had consulted with anyone that knows anything about password security, this would not have happened,” said Paul Kocher, president of Cryptography Research, a San Francisco computer security firm. [...]
LinkedIn does not have a chief security officer whose sole job it is to monitor for breaches. The company says David Henke, its senior vice president for operations, oversees security in addition to other roles, but Mr. Henke declined to speak for this article. [...]
The Register - 35m Google Profiles dumped into private database (25 May 2011)[edit]
In order to demonstrate that online information is trivial to mine, a Phd student from the University of Amsterdam in one month dumped the names, email addresses and biographical information of 35 million google profiles into a database. This was a experiment to test how difficult it would be to do and the answer was, not hard at all. The article does into some technical detail explaining why and how Google profiles in particular were vulnerable.
The New York Times - After Breach, Companies Warn of E-Mail Fraud (Epsilon breach) (04 April 2013)[edit]
Similar article by the WTJ with a slightly more business angle on it: http://online.wsj.com/article/SB10001424052748704587004576245131531712342.html and for a list of companies that had used Epsilon and had their email lists stolen: http://www.securityweek.com/massive-breach-epsilon-compromises-customer-lists-major-brands.
Articles describing a breach of Epsilon, an online marketing form (data broker) that handles email marketing for big firms such as JP Morgan Chase, Target, ... had been hacked and unencrypted email addresses had been stolen. In some cases names of the email addresses also which makes "spear phishing" a lot more effective as the phishing attack knows you have an account with company X, uses your name, perhaps even your address, making it much more likely that you will assume the email to be legitimate.
Wikipedia Article - Data breach: Major incidents[edit]
Wikipedia Fr - Piratage du PlayStation Network[edit]
Surveillance, the state and legislation addressing data collection[edit]
Big Brothrt Watch - Safe in Police Hands (July 2016)[edit]
How Police Forces suffer 10 data breaches every week and still want more of your data.
[edit]
A federal spy agency inadvertently shared logs of Canadians’ phone calls and Internet exchanges with intelligence allies such as the United States for years, a newly disclosed report says.
Just Security - EU-Funded Study: Electronic Mass Surveillance Fails – Drastically (14 October 2014)[edit]
Electronic mass surveillance – including the mass trawling of both metadata and content by the US National Security Agency – fails drastically in striking the correct balance between security and privacy that American officials and other proponents of surveillance insist they are maintaining.
BBC - Privacy fears over FBI facial recognition database (15 April 2014)[edit]
Campaigners have raised privacy concerns over a facial recognition database being developed by the FBI that could contain 52m images by 2015. […]
"This means that even if you have never been arrested for a crime, if your employer requires you to submit a photo as part of your background check, your face image could be searched - and you could be implicated as a criminal suspect, just by virtue of having that image in the non-criminal file," said the EFF. […]
The New York Times - Data privacy: US revelations put heat on business (23 February 2014)[edit]
Detailed article that describes the effect the revelations about government surveillance has had on the public's awareness of data collection by private companies, profits made from and the lack of protection of these.
BBC News - Tesco petrol stations use face-scan tech to target ads (4 November 2013)[edit]
At Tesco petrol stations in the UK, faces of customers will be scanned in order to target advertisement. The company says that customers will be asked to opt in but privacy concerns are being raised.
The New York Times - Europe Aims to Regulate the Cloud - (6 October 2013)[edit]
This article focuses mostly on the affects that proposals to the new EU regulation on data protection might have on cloud computing. It raises pertinent question such as what the consequences will be for EU companies with subsidiaries in the US and vice versa. Although the link makes an explicit link with Snowden's revelations, it is unclear to what extent the writer sees the new regulation as addressing concerns of data collection in the name of national security (which it is meant to not address) vs. data collection by private firms.
Bloomberg - U.K. Seeks to Block EU Data-Protection Plans That ‘Burden’ Firms (27 September 2013)[edit]
This article represents the point of view taken by some businesses, namely Google and Facebook, that argue that the new European legislation proposed by the European Commission and which is making its way through the European Parliament, would harm businesses by raising their costs.
The Guardian Newspaper Britain accused of trying to impede EU data protection law (27 September 2013)[edit]
Article dealing pretty much with the same argument but focusing instead on the interests of spy agencies to prevent too much data protection. The article also mentions 'safe harbour' which had been an agreement between the EU and the USA and which, after the Snowden leaks, has come under renewed scrutiny.
The Washington Post - NSA collects millions of e-mail address books globally (15 October 2013)[edit]
The National Security Agency is harvesting hundreds of millions of contact lists from personal e-mail and instant messaging accounts around the world, many of them belonging to Americans, according to senior intelligence officials and top-secret documents provided by former NSA contractor Edward Snowden. […]
During a single day last year, the NSA’s Special Source Operations branch collected 444,743 e-mail address books from Yahoo, 105,068 from Hotmail, 82,857 from Facebook, 33,697 from Gmail and 22,881 from unspecified other providers, according to an internal NSA PowerPoint presentation. […]
[…] the agency captures contact lists “on the fly” as they cross major Internet switches […]
The Wall Street Journal - French Privacy Agency Moves to Sanction Google (27 September 2013)[edit]
An article about the recent legal procedure initiated against Google Inc. by the French organisation Commission Nationale de l'Informatique et des Libertés, or CNIL, (http://www.cnil.fr/english/). The action focuses on the lack of transparency in Google's use of data collected. The article states that Google had introduced changes to its privacy data regulations in order to make its different products more compatible and as advertisers are increasingly turning away from other forms of advertising (e.g. TV ads), this data is becoming more valuable. The article overviews other European procedures against Google. See also NYTimes article 22 April 2013 below for similar developments in Germany.
Computer World - Google knows nearly every Wi-Fi password in the world (12 September 2013)[edit]
A short article reports that given the default setting on most of the millions of Android phones in the world, google is now probably in possession of very many of the world's wifi passwords. The default setting is to "back up your data" which means that quite a bit of personal information stored on your phone, including wifi passwords, is backed up with google. Given that the passwords are not well encrypted, and surely google is well able to decrypt them, this means that google has potentially access to very very many millions of wifi passwords. The article also lists several other articles that deal with the same issue.
New York Times - Germany Fines Google Over Data Collection (22 April 2013)[edit]
An article that starts with the 145 000 Euro fine Google received from a German court with regard to illegally collecting personal data during it's street view recording. It then does a quick overview of reactions by other countries to the disclosure that street view collected personal data. The article then considers approaches by other west European countries on the matter and efforts by the European institutions to introduce European legislation on the issue which would, amongst other things, raise the amount by which fines could in the future be levied on organizations.
Harvard Law Review: The Dangers of Surveillance (2012)[edit]
"From the Fourth Amendment to George Orwell’s Nineteen Eighty-Four, and from the Electronic Communications Privacy Act to films like Minority Report and The Lives of Others, our law and literature are full of warnings about state scrutiny of our lives. These warnings are commonplace, but they are rarely very specific. Other than the vague threat of an Orwellian dystopia, as a society we don’t really know why surveillance is bad, and why we should be wary of it. To the extent the answer has something to do with “privacy,” we lack an understanding of what “privacy” means in this context, and why it matters. We’ve been able to live with this state of affairs largely because the threat of constant surveillance has been relegated to the realms of science fiction and failed totalitarian states."
ZDNET : China's new data protection rules good step, but little bite (September 27, 2013)[edit]
Summary (quoted from website): "China has introduced rules to regulate the collection and use of personal data by its internet and telecoms operators. The rules have been a long time coming, but do they actually offer anything to users?"
Effects of loss of privacy on employment and credit worthiness[edit]
Ars Technica - Denied for that loan? Soon you may thank online data collection (11 October 2013)[edit]
Article based on a presentation given by Kate Crawford, a principal at Microsoft Research, at MIT’s EmTech conference. It visits two main points. Firstly, what data can be used for with regard to discrimination against persons on the base of what is known of them through online gathered data (e.g. loan decisions). Secondly, it considers the weakness of anonymization.
On Device Research - Facebook costing 16-34s jobs in tough economic climate (29 May 2013)[edit]
The index which covers 6000 16-34 year olds across six countries revealed some surprising results [: ] If getting a job was not hard enough in this tough economic climate, one in ten young people have been rejected for a job because of their social media profile.
CNN - Facebook friends could change your credit score (27 August 2013)[edit]
An article on the uses by financial companies of 'personal' data collected from Facebook, eBay... or even how you fill in an online application form. Amongst other the argument is made by representatives of these companies that this data is reliable enough, especially when taken as a whole, to have good enough idea of a person's creditworthiness.
Spiegel Online - Puny Punishment for Goliath: Google Case Exposes Weak US Data Privacy Laws (10 August 2012)[edit]
"Google has been forced to pay $22 million in fines this week, a record for data privacy violations but small change for the giant corporation. Internet companies benefit from America's lax privacy and data protection laws, which are unlikely to change any time soon. It's a stark contrast to Europe, where the EU wants to toughen its laws -- and apply them to American companies."
General studies[edit]
The Guardian - Google can remotely bypass the passcode of at least 74% of Android devices if ordered (23 November 2015)[edit]
According to a document prepared by the New York District Attorney’s Office, older versions of Android can easily be remotely reset by Google if compelled by a court order, allowing investigators to easily view the contents of a device.
The Guardian - Obfuscation: how leaving a trail of confusion can beat online surveillance (24 October 2015)[edit]
At the heart of Cambridge University, there’s a library tower filled with 200,000 forgotten books. Rumoured by generations of students to hold the campus collection of porn, Sir Gilbert Scott’s tower is, in fact, filled with pocket books. Guides, manuals, tales and pamphlets for everyday life, deemed insufficiently scholarly for the ordinary collection, they stand preserved as an extraordinary relic of past preoccupations.
International Journal of Communication - Exposing the Hidden Web: An Analysis of Third-Party HTTP Requests on One Million Websites(october 2015)[edit]
This article provides a quantitative analysis of privacy compromising mechanisms on one million popular websites. Findings indicate that nearly nine in ten websites leak user data to parties of which the user is likely unaware of; over six in ten websites spawn third-party cookies; and over eight in ten websites load Javascript code from external parties onto users’ computers. Sites which leak user data contact an average of nine external domains, indicating users may be tracked by multiple entities in tandem. By tracing the unintended disclosure of personal browsing histories on the web, it is revealed that a handful of American companies receive the vast bulk of user data. Finally, roughly one in five websites are potentially vulnerable
Ars Technica - Surveillance-based manipulation: How Facebook or Google could tilt elections (26 February 2015)[edit]
Someone who knows things about us has some measure of control over us, and someone who knows everything about us has a lot of control over us. Surveillance facilitates control.
Manipulation doesn’t have to involve overt advertising. It can be product placement that makes sure you see pictures that have a certain brand of car in the background. Or just increasing how often you see those cars. This is, essentially, the business model of search engines. In their early days, there was talk about how an advertiser could pay for better placement in search results. After public outcry and subsequent guidance from the FTC, search engines visually differentiated between “natural” results by algorithm and paid results. So now you get paid search results in Google framed in yellow and paid search results in Bing framed in pale blue. This worked for a while, but recently the trend has shifted back. Google is now accepting money to insert particular URLs into search results, and not just in the separate advertising areas. We don’t know how extensive this is, but the FTC is again taking an interest.
The Guardian - Facebook reveals news feed experiment to control emotions (30 June 2014)[edit]
It already knows whether you are single or dating, the first school you went to and whether you like or loathe Justin Bieber. But now Facebook, the world's biggest social networking site, is facing a storm of protest after it revealed it had discovered how to make users feel happier or sadder with a few computer key strokes.
Information.dk - For the NSA, espionage was a means to strengthen the US position in climate negotiations (30 January 2014)[edit]
At the Copenhagen Climate Summit in 2009, the world's nations were supposed to reach an agreement that would protect future generations against catastrophic climate change. But not everyone was playing by the rules. A leaked document now reveals that the US employed the NSA, its signals intelligence agency, to intercept information about other countries' views on the climate negotiations before and during the summit. According to observers, the spying may have contributed to the Americans getting their way in the negotiations.
George Washington University Law School - 'I've Got Nothing to Hide' and Other Misunderstandings of Privacy (2007)[edit]
Academic paper that undermines the 'nothing to hide' argument when asked about government surveillance. Professor Daniel Solove critiques the definition of 'privacy' found in the litterature and shows that some attempts to conceptualize privacy were too narrow, excluding things we commonly understand to be private and on the other hand, some attempts to conceptualize privacy are far too broad, such as Samuel Warren and Louis Brandeis's understanding of privacy as the "right to be let alone". In this essay, the author argued that instead of conceptualizing privacy with the traditional method, we should instead understand privacy as a set of family resemblances and eventually the author propose a taxonomy of privacy as given below:
- Information Collection
- Surveillance
- Interrogation
- Information Processing
- Aggregation
- Identification
- Insecurity
- Secondary Use
- Exclusion
- Information Dissemination
- Breach of Confidentiality
- Disclosure
- Exposure
- Increased Accessibility
- Blackmail
- Appropriation
- Distortion
- Invasion
- Intrusion
- Decisional Interference
The taxonomy has four general categories of privacy problems with sixteen different subcategories. The first general category is information collection, which involves the ways that data is gathered about people. The subcategories, surveillance and interrogation, represent the two primary problematic ways of gathering information. A privacy problem occurs when an activity by a person, business, or government entity creates harm by disrupting valuable activities of others. These harms need not be physical or emotional; they can occur by chilling socially beneficial behavior (for example, free speech and association) or by leading to power imbalances that adversely affect social structure (for example, excessive executive power).
The second general category is information processing. This involves the storing, analysis, and manipulation of data. There are a number of problems that information processing can cause, and the author included five subcategories in my taxonomy. For example, one problem that the author label insecurity results in increasing people’s vulnerability to potential abuse of their information. The problem that the author calls exclusion involves people’s inability to access and have any say in the way their data is used.
Information dissemination is the third general category. Disseminating information involves the ways in which it is transferred—or threatened to be transferred—to others. the author identifies seven different information dissemination problems.
Finally, the last category involves invasions. Invasions are direct interferences with the individual, such as intruding into her life or regulating the kinds of decisions she can make about her life.
The deeper problem with the nothing to hide argument is that it myopically views privacy as a form of concealment or secrecy. But understanding privacy as a plurality of related problems demonstrates that concealment of bad things is just one among many problems caused by government programs such as the NSA surveillance and data mining. In the categories in the taxonomy, several problems are implicated.
Harvard Law Review - The Dangers of Surveillance (2012)[edit]
Article by Neil M. Richards, from the Washington University School of Law, on the dangers of surveillance. "Surveillance is harmful because it can chill the exercise of our civil liberties, and because it gives the watcher power over the watched." He proposes "principles that should guide the future development of surveillance law, allowing for an appropriate balance between the costs and benefits of government surveillance."
First, [...] surveillance transcends the public private divide. [...] Even if we are ultimately more concerned with government surveillance, any solution must grapple with the complex relationships between government and corporate watchers.
Second, we must recognize that secret surveillance is illegitimate and prohibit the creation of any domestic surveillance programs whose existe nce is secret.
Third, [...] total surveillance is illegitimate and [it is not] acceptable for the government to record all internet activity without authorization. [...]
Fourth, [...] surveillance is harmful. [...] Reducing the harms of surveillance to doctrine in this way is essential if we want to avoid sacrificing our vital civil liberties
TED talks - The internet, the perfect tool for the surveillance state? Further reading (and watching) on the state of digital privacy (7 November 2013)[edit]
A list of three talks that attempt to summarise issues surrounding digital privacy. By Mikko Hypponen, Bruce Schneier and Alessandro Acquisti.
Electronic Frontier Foundation (EFF) - Who has your back? (continuously updated)[edit]
This website lists the largest online companies and how their reported attitude with regard to privacy. For instance it awards stars for companies that attempted to defend against data requests by spy agencies.
MIT Technological Review - The real privacy problem (22 October 2013)[edit]
A detailed and long article analysing questions surrounding the privacy debate. A lot of good links to other articles, books and other sources as well as historical context to the debate on the interplay between privacy and democracy.
"So if you want to defend the “right to privacy” for its own sake, turning data into a tradable asset could resolve your misgivings. The NSA would still get what it wanted; but if you’re worried that our private information has become too liquid and that we’ve lost control over its movements, a smart business model, coupled with a strong digital-rights-management regime, could fix that."
Boston College Law Review - Big Data and Due Process: Toward a Framework to Redress Predictive Privacy Harms (13 September 2013)[edit]
"The rise of “big data” analytics in the private sector poses new challenges for privacy advocates. Unlike previous computational models that exploit personally identifiable information (PII) directly, such as behavioral targeting, big data has exploded the definition of PII to make many more sources of data personally identifiable. By analyzing primarily metadata, such as a set of predictive or aggregated findings without displaying or distributing the originating data, big data approaches often operate outside of current privacy protections (Rubinstein 2013; Tene and Polonetsky 2012), effectively marginalizing regulatory schema. Big data presents substantial privacy concerns – risks of bias or discrimination based on the inappropriate generation of personal data – a risk we call “predictive privacy harm.” Predictive analysis and categorization can pose a genuine threat to individuals, especially when it is performed without their knowledge or consent. While not necessarily a harm that falls within the conventional “invasion of privacy” boundaries, such harms still center on an individual’s relationship with data about her. Big data approaches need not rely on having a person’s PII directly: a combination of techniques from social network analysis, interpreting online behaviors and predictive modeling can create a detailed, intimate picture with a high degree of accuracy. Furthermore, harms can still result when such techniques are done poorly, rendering an inaccurate picture that nonetheless is used to impact on a person’s life and livelihood."
The Boston Consulting Group - The Value of Our Digital Identity (20 November 2012)[edit]
The Value of Our Digital Identity, a new report by The Boston Consulting Group in the Liberty Global Policy Series, takes a unique approach to understanding this new phenomenon. It quantifies, for the first time, the current and potential economic value of digital identity. It also explores—through research involving more than 3,000 individuals—the value that consumers place on their personal information and how they make decisions about whether or not to share it. Building on these findings, the report presents a new paradigm for unlocking the full value of digital identity in a sustainable, consumer-centered way. [...]
The report shows that the value created through digital identity can indeed be massive: €1 trillion in Europe by 2020 [...]
Given proper privacy controls and sufficient benefits, the survey found, most consumers are willing to share their personal data. To ensure that the flow of personal information continues, organizations therefore need to make the benefits clear to consumers. They also need to embrace responsibility, transparency, and user control. [...]
The Cost of Reading Privacy Policies. I/S: A Journal of Law and Policy for the Information Society 2008 Privacy Year in Review issue. (with A. McDonald) http://lorrie.cranor.org/#publications Download: http://lorrie.cranor.org/pubs/readingPolicyCost-authorDraft.pdf[edit]
It would take each American 244 hours per year to read privacy policies… cf. page 18. About 40 minutes every day.
Other[edit]
EFF - Police Around the Country Regularly Abuse Law Enforcement Databases - 28 September 2016[edit]
For more than a year, EFF has been investigating how police in California misuse the state’s law enforcement database with little oversight from officials. An investigation published by the Associated Press today shows that abuse of law enforcement systems is a nationwide problem.
Ars Technica - Major Qualcomm chip security flaws expose 900M Android users - 8 August 2016[edit]
Four major security holes in the Qualcomm chips which power modern Android devices have left as many as 900 million users vulnerable to a range of attacks.
The Guardian - Your battery status is being used to track you online - 2 August 2016[edit]
A little-known web standard that lets site owners tell how much battery life a mobile device has left has been found to enable tracking online, a year after privacy researchers warned that it had the potential to do just that.
The Guardian - Chinese university puts CCTV in dormitories to encourage 'good study habits' (16 June 2016)[edit]
A university in central China has reportedly been using surveillance cameras to monitor virtually every inch of its 73-hectare (181-acre) campus, including its classrooms and dormitories. The Wuchang University of Technology in the city of Wuhan reportedly introduced the technology last year, paying 6 million yuan (about £645,000) in order to keep closer tabs on its 12,500 undergraduates. A 100-strong team of officials has been tasked with monitoring the images as they are captured, according to a report on cnhubei.com, a news website in Hubei province, where the university is located. Sun Yi, from the university’s business school, said the move was designed to encourage “good study habits” among students.
CBC - BlackBerry hands over user data to help police 'kick ass,' insider says (9 June 2016)[edit]
A specialized unit inside mobile firm BlackBerry has for years enthusiastically helped intercept user data — including BBM messages — to help in hundreds of police investigations in dozens of countries, a CBC News investigation reveals. CBC News has gained a rare glimpse inside the struggling smartphone maker's Public Safety Operations team, which at one point numbered 15 people, and has long kept its handling of warrants and police requests for taps on user information confidential.
The Intercept_ - The Secret Surveillance Catalogue (17 December 2015)[edit]
Concerned about the militarization of law enforcement, a source within the intelligence community has provided The Intercept with a secret, internal U.S. government catalogue of dozens of cellphone surveillance devices used by the military and by intelligence agencies. Some of the devices are already in use by federal law enforcement and local police forces domestically, and civil liberties advocates believe others will eventually find their way into use inside the U.S. This product catalogue provides rare insight into the current spy capabilities of local law enforcement and offers a preview of the future of mass surveillance of mobile communications.
WSJ - SocialRadar Balances Privacy With New Social Geolocation App (30 January 2014)[edit]
A guy walks into a bar and knows the name of the attractive woman across the room before he even says “hello.”
While the scenario may sound like the beginning of an old joke, it’s actually a new mobile app launching Thursday called SocialRadar.
Created by a Washington-based startup of the same name, the app collects information like employment, relationship status, education and music preferences from Twitter, Facebook, LinkedIn, Foursquare, Instagram and Google+. The app then blends that data with locations gleaned from users’ smartphones to present profiles of people nearby.
The New York Times - Letting Down Our Guard With Web Privacy (Psychology of divulging private information on the net) (30 March 2013)[edit]
Article considering the psychological reasons why we surrender more private information on the net than we would in real life.
The New Yorker - The Prism (24 June 2013)[edit]
Article that considers the history of society's understanding of privacy. It draws parallels with the 1844 scandal around the London government's opening of letters by an Italian resident. It also contrasts terms privacy with advertising, arguing that the two tendencies, contradictory, appear to be very strong in current US American society.
EuropaQuotidiano - Facebook, i Big Data e la fine della privacy
Euobserver - Academics line up to defend EU data protection law